
Virtual Private Servers (VPS) have become an integral part of web hosting, offering users a dedicated virtual environment with enhanced flexibility and control. However, the convenience of Secure VPS hosting comes with the responsibility of ensuring robust security measures to protect your data and applications. In this comprehensive guide, we will delve into various aspects of Secure VPS, covering everything from initial setup to ongoing maintenance.
Top 10 Tips for Secure VPS Hosting
1. Choosing a Secure VPS Provider
The first step in securing your VPS is selecting a reputable hosting provider. Look for providers with a track record of reliability and security. Consider factors such as data center locations, security certifications, and customer reviews. Opting for providers that offer regular security updates and employ advanced security technologies will significantly contribute to a secure hosting environment.
Cyberhosting is one of the most secure VPS hosting service providers for developers to quickly deploy sites to cloud servers like Vultr, Hetzner, and CyberHosting premium servers. Cyberhosting is renowned for its affordability and reliability. With a user-friendly interface and robust features, it caters to businesses of all sizes, from bloggers to large enterprises.
Cyberhosting offers:
- 24/7 Support Crazy-good support so you can focus on your project, not your server.
- WordPress is Fully optimized for lightning-fast WordPress sites.
- Security Fort Knox security is built-in as standard on every CyberHosting install.
- Great Value We don’t lock you in. Start low, and increase as you scale. Cancel any time.
- Read about our features here.
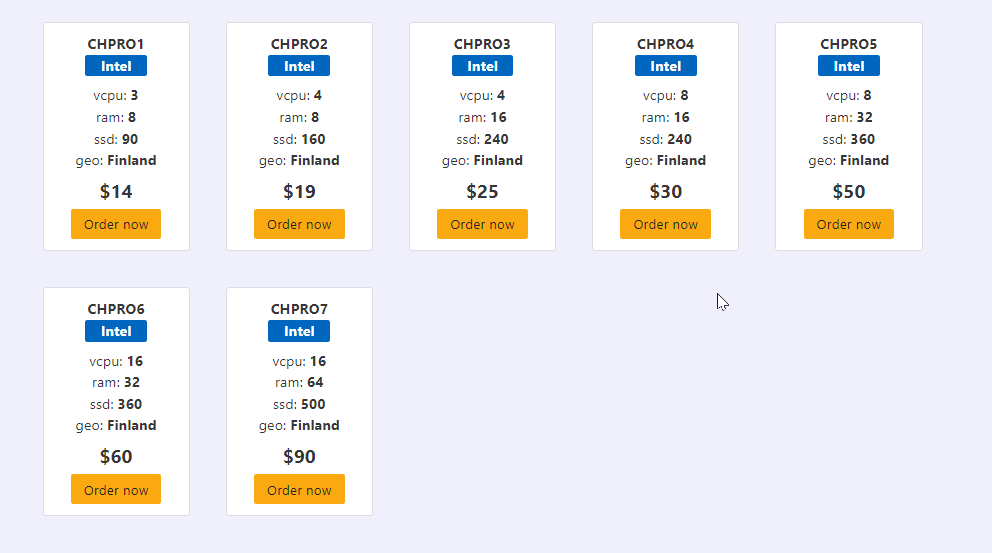
CyberHosting provides three distinct server options for your hosting needs. Our exclusive CyberHosting Premium servers commence at $14, offering 3 CPUs and 8 GB of RAM. This implies that obtaining a server with 1 CPU and 2 GB RAM will cost you less than $5. Below are the CyberHosting pricing plans.
CyberHosting Permuim Plan:
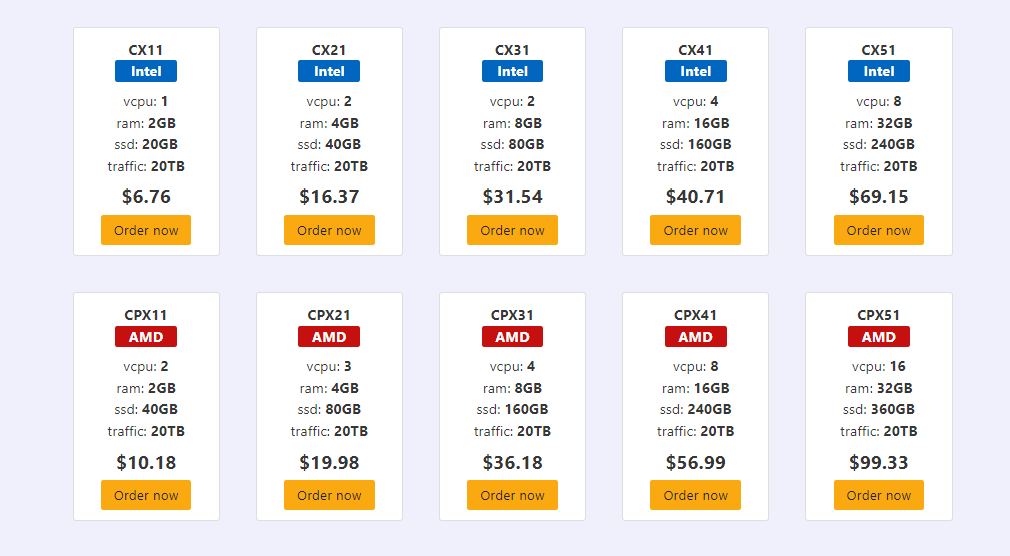
CyberHosting Hetnzer Plan:
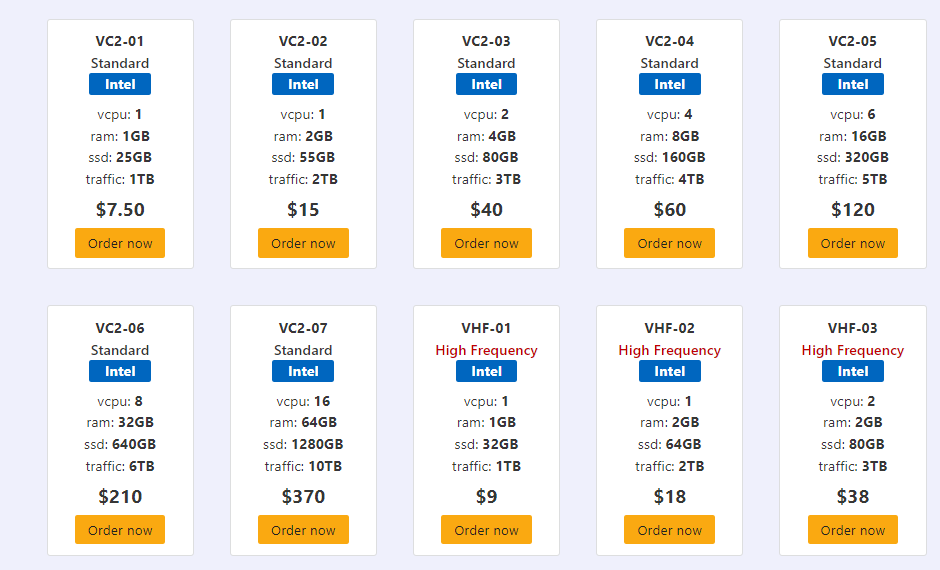
CyberHosting Vultr Plan:
2. Operating System Security

The choice of the operating system plays a crucial role in VPS security. Regularly update your operating system to patch known vulnerabilities. Consider using minimal installations to reduce the attack surface and remove unnecessary services and applications. Implementing a robust firewall, such as tables on Linux, is essential for controlling incoming and outgoing traffic.
3. Strong Authentication Mechanisms

Secure your VPS by implementing strong authentication mechanisms. Utilize secure SSH (Secure Shell) keys instead of password-based authentication to prevent brute-force attacks. Regularly rotate and update SSH keys, and consider implementing multi-factor authentication for an additional layer of security.
4. Regular Backups

Backup your data regularly to prevent data loss in case of a security incident. Implement automated backup solutions and store backups in a separate location from the VPS. This ensures that even if the VPS is compromised, your critical data remains secure and accessible.
5. Network Security
Configure your VPS network securely by using Virtual Private Networks (VPNs) and ensuring that only necessary ports are open. Disable unused services and regularly monitor network traffic for unusual patterns. Consider implementing intrusion detection and prevention systems to identify and mitigate potential security threats.
6. Updates and Patch Management

Regularly update and patch all software and applications running on your VPS to address known vulnerabilities. Enable automatic updates where possible and regularly check for updates manually. A proactive approach to patch management is crucial for maintaining a secure VPS environment.
7. Security Audits and Monitoring

Regularly conduct security audits to identify potential vulnerabilities and weaknesses in your VPS configuration. Implement continuous monitoring tools to detect and respond to security incidents promptly. Log and audit system activities to track any unauthorized access or suspicious behavior.
8. Secure File Permissions

Set appropriate file permissions to restrict access to sensitive files and directories. Follow the principle of least privilege, granting only the minimum necessary permissions to users and applications. Regularly audit and update file permissions to ensure ongoing security.
9. Security Best Practices for Web Applications
If your VPS hosts web applications, apply security best practices such as input validation, secure coding practices, and regular security assessments. Utilize web application firewalls to protect against common web-based attacks like SQL injection and cross-site scripting.
10. Physical Security Measures

Consider physical security measures to safeguard the physical hardware of your VPS. Choose data centers with robust physical security, including access controls, surveillance, and environmental controls. Additionally, encrypt sensitive data to protect it even if physical security measures fail.
Threat Intelligence and Incident Response
- Incorporating threat intelligence feeds to stay informed about emerging threats.
- Utilizing threat intelligence to proactively adjust security measures based on evolving cyber threats.
- Developing and regularly testing incident response plans to streamline reactions to security incidents.
- Establishing clear communication protocols and escalation procedures in the event of a security breach.
- Navigating regulatory frameworks (e.g., GDPR, HIPAA, PCI DSS) and aligning server security practices with compliance requirements.
- Adhering to data protection standards and ensuring server security aligns with legal and industry-specific regulations.
FAQs
What is VPS hosting, and why is security important?
VPS (Virtual Private Server) hosting is a type of hosting that offers a dedicated virtual environment within a larger physical server. Security is crucial to protect your data, and applications, and ensure the integrity of your hosting environment.
How do I choose a secure VPS provider?
Look for providers with a strong security track record, data center certifications, and positive customer reviews. Consider factors like regular security updates, advanced security technologies, and the reputation of the hosting provider.
What operating system security measures should I implement?
Regularly update your operating system, use minimal installations, and employ a robust firewall (e.g., iptables for Linux). Disable unnecessary services and applications to reduce the attack surface.
Why is strong authentication important, and how can I achieve it?
Strong authentication, such as SSH key-based authentication, enhances security by preventing brute force attacks. Regularly update and rotate SSH keys, and consider implementing multi-factor authentication for an additional layer of protection.
How often should I back up my data, and where should I store backups?
Regularly back up your data, and implement automated backup solutions. Store backups in a separate location from the VPS to ensure data recovery in case of a security incident.
Conclusion
Secure VPS is an ongoing process that requires a combination of preventive measures, proactive monitoring, and timely responses to emerging threats. By following the comprehensive steps outlined in this guide, you can establish a robust and secure VPS environment, safeguarding your data and applications from potential security risks.
Follow CyberHosting on Facebook / Twitter / Linkedin for updates.
